Historically Domain Name System (DNS) was built to use both TCP and UDP protocols on port 53. However for an ordinary client’s name resolution request, only UDP protocol is enough. According to internet traffic studies the ratio of DNS traffic is 19:1 in favor of UDP. Which means approximately 95% traffic is UDP and only 5% is TCP. If TCP protocol is blocked, 95% name resolution will work fine. As the time is passing DNS dependency on TCP protocol is increasing day by day. Also we cannot ignore remaining 5%. In short modern DNS Servers functionality depends on both TCP as well as UDP. Let’s understand the details.
When DNS Server Use UDP
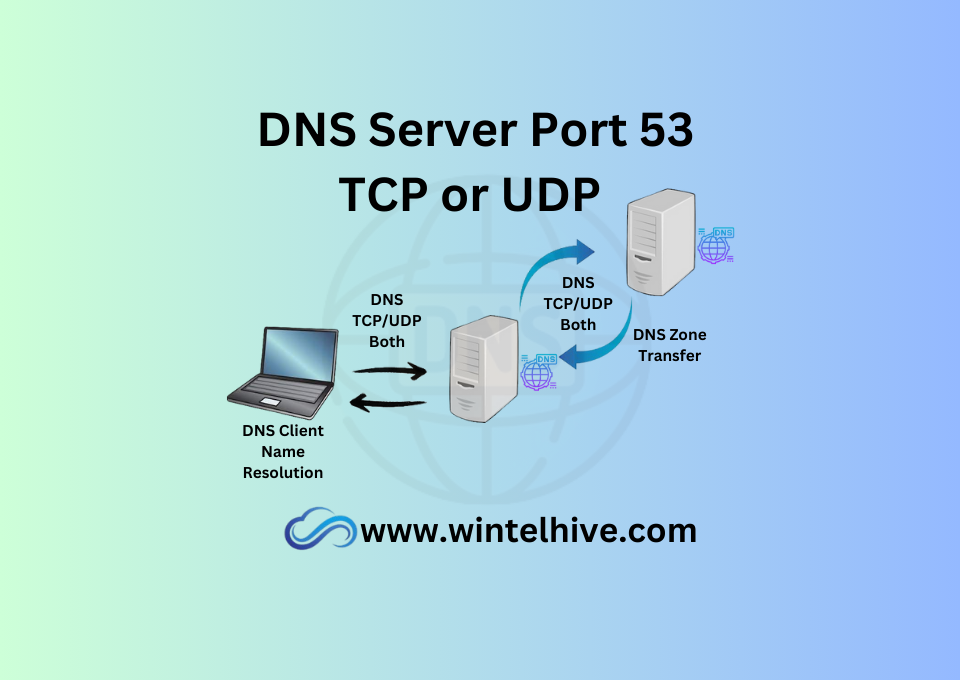
By default any client that want to resolve a DNS resource record, sends the request to domain name system on UDP protocol using network port 53. Servers resolves the name and send the response back to the client using a UDP packet. The maximum packet size of this UDP packet is 512 bytes.
When DNS Server Switch to TCP
In DNS UDP communication, there is neither initial handshake nor acknowledgement. As a result there is always a chance of packet loss during transmission. Because of absence of acknowledgment the probability of data loss is even higher which further makes UDP protocol less reliable for DNS communication. As a result, if the client does not receives a response from DNS server within 3 to 5 second. Client switch itself to TCP.
Historically DNS response packet size were usually small. Since it was containing little information. 512 bytes were enough in most of cases. But these days DNS packets may contain much larger information. Which does not fit in a single 512 bytes packet. Following are some of the common reasons of bigger packet size are,
- DNS servers host multiple resource records and return multiple records in response which makes packet size bigger.
- With increasing use of IPv6 day by, DNS servers return IPv4 and IPv6 both type of information together.
- Some DNS records contain long text. For example TXT contains a lot of text data which may be bigger than 512 bytes.
- If we have built secure DNS infrastructure using Domain Name System Security Extensions (DNSSEC) and zone-signing key (ZSK). Large packet size communication is very much expected.
Whatever is the reason. Main point is if server know, DNS response cannot be sent in 512 bytes. Solution is there in RFC-1035. DNS server will truncate the longer message and set the ‘TC bit’ in the header. This ‘TC bit” in the header is a message for the client that the message length is more than the originally allowed size. In this situation the client will resend the request to server on TCP. Now server will respond back using TCP. TCP supports much bigger packet size. As a result bigger data transmission becomes possible. Also TCP is a stateful protocol (means its support proper handshake and acknowledgement feature), so there is no chance of packet loss.
Firewall Settings for DNS
Firewall Settings for DNS Clients
Lets assume for a minute TCP 53 blocked between DNS client and server. Now DNS server want to transmit a large size packet. Either domain name system resolution will fail completely. Or DNS may use packet fragmentation on UDP. Packet fragmentation is a process of splitting bigger data in small pieces and transmitting them in more than one UDP packets. It may work, but it does not guarantee the accurate data delivery. So the correct way of configuring firewall is to allow TCP and UDP both for DNS server. We have often observed Information Security and Governance teams advice to open UDP 53 only on the firewall level. Enlighten them please, this is no longer valid.
Firewall Settings DNS Zone Transfer (Primary and Secondary)
If we have multiple DNS servers in our environment, the zone database must be consistent across all servers. To make sure all are servers are consistent and updated, they must sync with one master server. This is called DNS zone transfer process. When zone transfer happens between primary (Master) DNS sever and secondary (slave) server. The communication always on TCP network port 53. UDP can’t be used for this type of communication.
DNS Server Port Requirements Summary
To sum it up, we should to allow both TCP an UDP port 53 for a reliable, robust and secure name resolution. No matter if its a client server communication or server to server zone transfer.
Frequently Asked Question (FAQ)
No. DNS communication is not secure by default.
UDP is a stateless protocol. Much faster than TCP and works very well in 95% cases. When it does not serve the purpose. Client automatically switch to TCP.
Unidirectional port 53 traffic is enough for DNS client server communication.
UDP fragmentation is a process in which larger data is split between smaller pieces and transmitted over the network’s maximum transmission unit (MTU). This may cause delay or event data loss sometimes.
-
DNS Server – A detailed introduction
Understand DNS server. Installation, types of zones, resource records, failover, public/private DNS, conditional forwarders and much more.
-
DNS Port 53 TCP or UDP?
Ever wondered why DNS uses both TCP and UDP? Find out when DNS switches between TCP and UDP on port 53 and why it matters.
-
DNS Forwarder
Learn how a DNS forwarder can boost your network’s speed, improve security. Reduce load for better DNS management.








Leave a Reply